Author Archives: Malin Lundqvist
Smart pointers vs Raw pointers
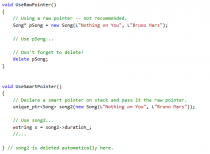
In c++ you use pointers very often, and they are the main reason for memory leaks and other problems. They allocate memory and if they are not deleted that is a memory leak. To avoid this problem the Smart pointers are to prefer.
A Smart pointer contains a Raw pointer – pointing to it, and it has the same size -, only the Smart pointer deletes the Raw pointer when it is no longer used. This means that you don’t have […]

Smart pointers vs Raw pointers
In c++ you use pointers very often, and they are the main reason for memory leaks and other problems. They allocate memory and if they are not deleted that is a memory leak. To avoid this problem the Smart pointers are to prefer.
A Smart pointer contains a Raw pointer – pointing to it, and it has the same size -, only the Smart pointer deletes the Raw pointer when it is no longer used. This means that you don’t have […]

Smart pointers vs Raw pointers
In c++ you use pointers very often, and they are the main reason for memory leaks and other problems. They allocate memory and if they are not deleted that is a memory leak. To avoid this problem the Smart pointers are to prefer.
A Smart pointer contains a Raw pointer – pointing to it, and it has the same size -, only the Smart pointer deletes the Raw pointer when it is no longer used. This means that you don’t have […]

Smart pointers vs Raw pointers
In c++ you use pointers very often, and they are the main reason for memory leaks and other problems. They allocate memory and if they are not deleted that is a memory leak. To avoid this problem the Smart pointers are to prefer.
A Smart pointer contains a Raw pointer – pointing to it, and it has the same size -, only the Smart pointer deletes the Raw pointer when it is no longer used. This means that you don’t have […]
Visual Leak Detector – File and line number not available
When using Visual Leak Detector (vld) there are some problems you might encounter. The problem (I thought I had) was that it wouldn’t show what file and line number it found the memory leaks in. No matter how much I searched for this on google no one seemed to give me an answer that worked.
When the running was done the top line of the vld output said (inside the green rectangle): “0x0F37C260 (File and line number not available): MSVCR120D.dll!operator […]
Visual Leak Detector – File and line number not available
When using Visual Leak Detector (vld) there are some problems you might encounter. The problem (I thought I had) was that it wouldn’t show what file and line number it found the memory leaks in. No matter how much I searched for this on google no one seemed to give me an answer that worked.
When the running was done the top line of the vld output said (inside the green rectangle): “0x0F37C260 (File and line number not available): MSVCR120D.dll!operator […]
Visual Leak Detector – File and line number not available
When using Visual Leak Detector (vld) there are some problems you might encounter. The problem (I thought I had) was that it wouldn’t show what file and line number it found the memory leaks in. No matter how much I searched for this on google no one seemed to give me an answer that worked.
When the running was done the top line of the vld output said (inside the green rectangle): “0x0F37C260 (File and line number not available): MSVCR120D.dll!operator […]
Visual Leak Detector – File and line number not available
When using Visual Leak Detector (vld) there are some problems you might encounter. The problem (I thought I had) was that it wouldn’t show what file and line number it found the memory leaks in. No matter how much I searched for this on google no one seemed to give me an answer that worked.
When the running was done the top line of the vld output said (inside the green rectangle): “0x0F37C260 (File and line number not available): MSVCR120D.dll!operator […]
Recursion
This week in programming we have learnt about Binary Search Trees (BST). While creating the program for a BST recursion is a great method to know and to use. Recursion is when a method calls itself from inside. You can read more about it on wikipedias page about recursion: http://en.wikipedia.org/wiki/Recursion_%28computer_science%29
I thought I could go through how I wrote my code to find the node to erase in the tree and why I chose to do it in that way. […]
Recursion
This week in programming we have learnt about Binary Search Trees (BST). While creating the program for a BST recursion is a great method to know and to use. Recursion is when a method calls itself from inside. You can read more about it on wikipedias page about recursion: http://en.wikipedia.org/wiki/Recursion_%28computer_science%29
I thought I could go through how I wrote my code to find the node to erase in the tree and why I chose to do it in that way. […]
Recursion
This week in programming we have learnt about Binary Search Trees (BST). While creating the program for a BST recursion is a great method to know and to use. Recursion is when a method calls itself from inside. You can read more about it on wikipedias page about recursion: http://en.wikipedia.org/wiki/Recursion_%28computer_science%29
I thought I could go through how I wrote my code to find the node to erase in the tree and why I chose to do it in that way. […]
Recursion
This week in programming we have learnt about Binary Search Trees (BST). While creating the program for a BST recursion is a great method to know and to use. Recursion is when a method calls itself from inside. You can read more about it on wikipedias page about recursion: http://en.wikipedia.org/wiki/Recursion_%28computer_science%29
I thought I could go through how I wrote my code to find the node to erase in the tree and why I chose to do it in that way. […]

The Knytt Stories Assignment
Introduction
This rapport is about a group assignment by me, Malin Lundqvist, and my teammate, Simon Strandh. The assignment was to make a game using the Knytt Stories level editor and the restrictions were; the game cannot take more than 15 minutes to play and no text or signs were to be used. We had three weeks to complete the assignment.
We came up with the story of a princess who got afraid of taking the responsibility of being queen and the […]

The Knytt Stories Assignment
Introduction
This rapport is about a group assignment by me, Malin Lundqvist, and my teammate, Simon Strandh. The assignment was to make a game using the Knytt Stories level editor and the restrictions were; the game cannot take more than 15 minutes to play and no text or signs were to be used. We had three weeks to complete the assignment.
We came up with the story of a princess who got afraid of taking the responsibility of being queen and the […]

The Knytt Stories Assignment
Introduction
This rapport is about a group assignment by me, Malin Lundqvist, and my teammate, Simon Strandh. The assignment was to make a game using the Knytt Stories level editor and the restrictions were; the game cannot take more than 15 minutes to play and no text or signs were to be used. We had three weeks to complete the assignment.
We came up with the story of a princess who got afraid of taking the responsibility of being queen and the […]

The Knytt Stories Assignment
Introduction
This rapport is about a group assignment by me, Malin Lundqvist, and my teammate, Simon Strandh. The assignment was to make a game using the Knytt Stories level editor and the restrictions were; the game cannot take more than 15 minutes to play and no text or signs were to be used. We had three weeks to complete the assignment.
We came up with the story of a princess who got afraid of taking the responsibility of being queen and the […]

Betrayal at House on the Hill, board game analysis number two.
Betrayal at House on the Hill is a board game with two phases. In the first phase you and the other players work together to explore the house and find all the things that is hidden inside. In the other phase one of the players will turn into a traitor, he or she might turn into a monster or maybe he or she will create a monster haunting you. Or you might all still be friends and the house turns […]

Betrayal at House on the Hill, board game analysis number two.
Betrayal at House on the Hill is a board game with two phases. In the first phase you and the other players work together to explore the house and find all the things that is hidden inside. In the other phase one of the players will turn into a traitor, he or she might turn into a monster or maybe he or she will create a monster haunting you. Or you might all still be friends and the house turns […]

Betrayal at House on the Hill, board game analysis number two.
Betrayal at House on the Hill is a board game with two phases. In the first phase you and the other players work together to explore the house and find all the things that is hidden inside. In the other phase one of the players will turn into a traitor, he or she might turn into a monster or maybe he or she will create a monster haunting you. Or you might all still be friends and the house turns […]

Betrayal at House on the Hill, board game analysis number two.
Betrayal at House on the Hill is a board game with two phases. In the first phase you and the other players work together to explore the house and find all the things that is hidden inside. In the other phase one of the players will turn into a traitor, he or she might turn into a monster or maybe he or she will create a monster haunting you. Or you might all still be friends and the house turns […]

Kill doctor Lucky, board game analysis
“Kill doctor Lucky” is a game for 3-7 players where the player who succeeds to kill the doctor wins. Moving around in his mansion you have to make sure that no one can see you while you’re in the same room as the doctor, that’s when you can strike and make an attempt to kill him. Although his dog follows him everywhere, and can actually prevent a murder on the doctor, he has short legs and sometimes falls behind as […]

Kill doctor Lucky, board game analysis
“Kill doctor Lucky” is a game for 3-7 players where the player who succeeds to kill the doctor wins. Moving around in his mansion you have to make sure that no one can see you while you’re in the same room as the doctor, that’s when you can strike and make an attempt to kill him. Although his dog follows him everywhere, and can actually prevent a murder on the doctor, he has short legs and sometimes falls behind as […]

Kill doctor Lucky, board game analysis
“Kill doctor Lucky” is a game for 3-7 players where the player who succeeds to kill the doctor wins. Moving around in his mansion you have to make sure that no one can see you while you’re in the same room as the doctor, that’s when you can strike and make an attempt to kill him. Although his dog follows him everywhere, and can actually prevent a murder on the doctor, he has short legs and sometimes falls behind as […]

Kill doctor Lucky, board game analysis
“Kill doctor Lucky” is a game for 3-7 players where the player who succeeds to kill the doctor wins. Moving around in his mansion you have to make sure that no one can see you while you’re in the same room as the doctor, that’s when you can strike and make an attempt to kill him. Although his dog follows him everywhere, and can actually prevent a murder on the doctor, he has short legs and sometimes falls behind as […]